Hackers have unleashed a major cyber attack causing huge disruption to companies and governments across the globe including in the UK, US and Russia.
The Petya ransomware hijacks victims’ computers before encrypting their files and holding them hostage until a fee is paid.
Chernobyl’s radiation monitoring system has been hit by the attack with its sensors shut down, while UK advertising giant WPP, the largest agency in the world, among dozens of firms affected.
The ransomware appears to have been spread through popular accounting software and specifically targeted at bringing down business IT systems.
The outage began in Ukraine as the country’s power grid, airport, national bank and communications firms were first to report problems, before it spread rapidly throughout Europe.
Companies in the US, Germany, Norway, Russia, Denmark and France are among those to have confirmed issues so far.
It comes just weeks after the WannaCry attack, which left hundreds of thousands of users around the world unable to access their data.
More than 200,000 victims in 150 countries were infected by that software, which originated in the UK and Spain last month, before spreading globally.
But cyber security experts have warned that this time the virus is much more dangerous, because it has no “kill switch” and is designed to spread rapidly though networks.
Marcus Hutchins, who foiled the previous WannaCry attack by discovering a way to stop it from infecting new computers, told MailOnline that even if users pay the fee their files could now be lost forever.

He said: “The company that hosts the email account which the ransomware asks you to contact has closed the account. There’s no way to get files back.
“It’s early days – we don’t know if we can find a fix yet. But if it’s decryptable we will find a way.”
Hutchins, 22, continued: “Everyone’s looking at this right now and I’m working with other researchers. I was just praying it wasn’t the Wannacry exploit again. Ideally, we’ll have to find a way to decrypt the files or else people are not going to get them back.”
The ransomware targets computers using the Windows XP operating system, which have not installed the latest security updates released by Microsoft.
Experts fear that could mean major infrastructure such as healthcare systems and power networks using archaic technology will be the worst affected.
Russia’s Rosneft oil company and steel firm Evraz, Danish shipping giant A.P. Moller-Maersk, and global law firm DLA Piper confirmed issues, along with French industrial group Saint-Gobain.
Radiation checks at the Chernobyl nuclear disaster site in Ukraine were being carried out manually after the wave of cyber attacks.
A spokesman said: “Due to the temporary disconnection of Windows systems, radiation monitoring of the industrial site is being carried out manually.”
Rozenko Pavlo, Ukraine’s deputy Prime Minister, posted an image of his locked computer, saying “all computers of the government” had fallen victim to the virus.
An image he uploaded shows a black screen covered in white text which warns that “one of your disks contains errors and needs to be repaired”.

The screen also warns not to turn the computer off otherwise all data will be lost.
He called the attack “unprecedented”, though said vital services would not be affected.
Another screen with red text warns that files on the computer have been encrypted and will only be released if a payment of £300 in anonymous online currency Bitcoin is made.
Oleksandr Turchynov, head of Ukraine’s national security council, immediately pointed the finger at Moscow, saying: “Already on first analysis it is possible to talk of Russian fingerprints.”
Anders Rosendahl, a spokesman for Copenhagen-based AP Moller-Maersk, said: “We are talking about a cyberattack. It has affected all branches of our business, at home and abroad.”
Cyber security expert Daniel Gallagher told MailOnline: “We are still in the early stages of determining the scope of impact, though there are indications that it is rapidly spreading.
“I think we will see a different kind of impact, since Wannacry had the side effect of forcing a lot of locations to patch their computers. The areas we will likely see impacted could be some of the worst though.
“They will be the locations that for some reason or another could not afford to patch in a timely manner. Places that may have industrial controls or other critical infrastructure that can’t easily be taken offline to upgrade.”
Such viruses hold data to ransom, scrambling it until a payment is made, usually requesting virtual currency Bitcoin because it cannot be traced to a user.
The world is still recovering from a previous outbreak of ransomware, called WannaCry or WannaCrypt, which spread rapidly using digital break-in tools originally created by the U.S. National Security Agency and recently leaked to the web.
While experts cannot definitively say where that attack originated, information hidden in the code used to run in pointed to the involvement of North Korea.
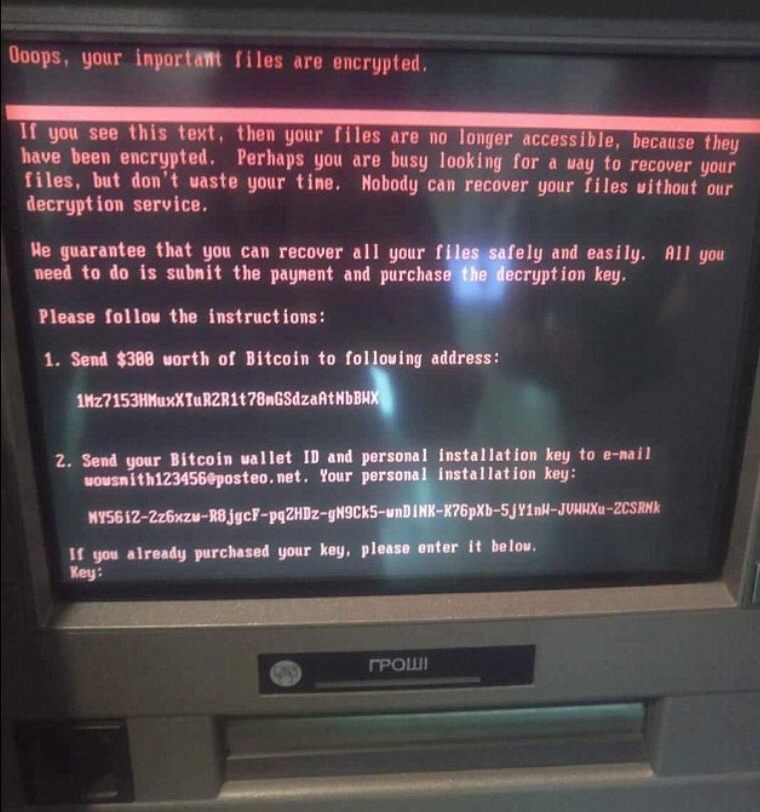 Message displayed on a computer screen in Ukraine
Message displayed on a computer screen in Ukraine 





